Mission Control Blog

Organizations are transitioning to the cloud faster than ever to keep up with the changing consumer and business climate. According to Gartner, by 2023, 40% of all
- CSPM
- CAASM

JupiterOne aggregates and normalizes data from hundreds of different sources so you can identify and triage security risks easily.

It seems like a simple question. “Are any of our deployed user endpoint devices missing an endpoint detection and response agent?”

At the most basic level of the Incident Response Hierarchy, security teams must know the assets they are defending.
- CAASM

Natural language search leverages AI to bring ease of use to the forefront of the JupiterOne platform.

Here’s our recap of Black Hat, BSides and DEFCON, otherwise known as Hacker Summer Camp 2023!

As companies move to the cloud, continuous compliance efforts - which may feel like an obstacle - can become an accelerator in the migration process.

It's more likely today that cloud-enabled businesses need to pay attention to compliance frameworks like SOC 2 to protect themselves and their customers.
- GRC
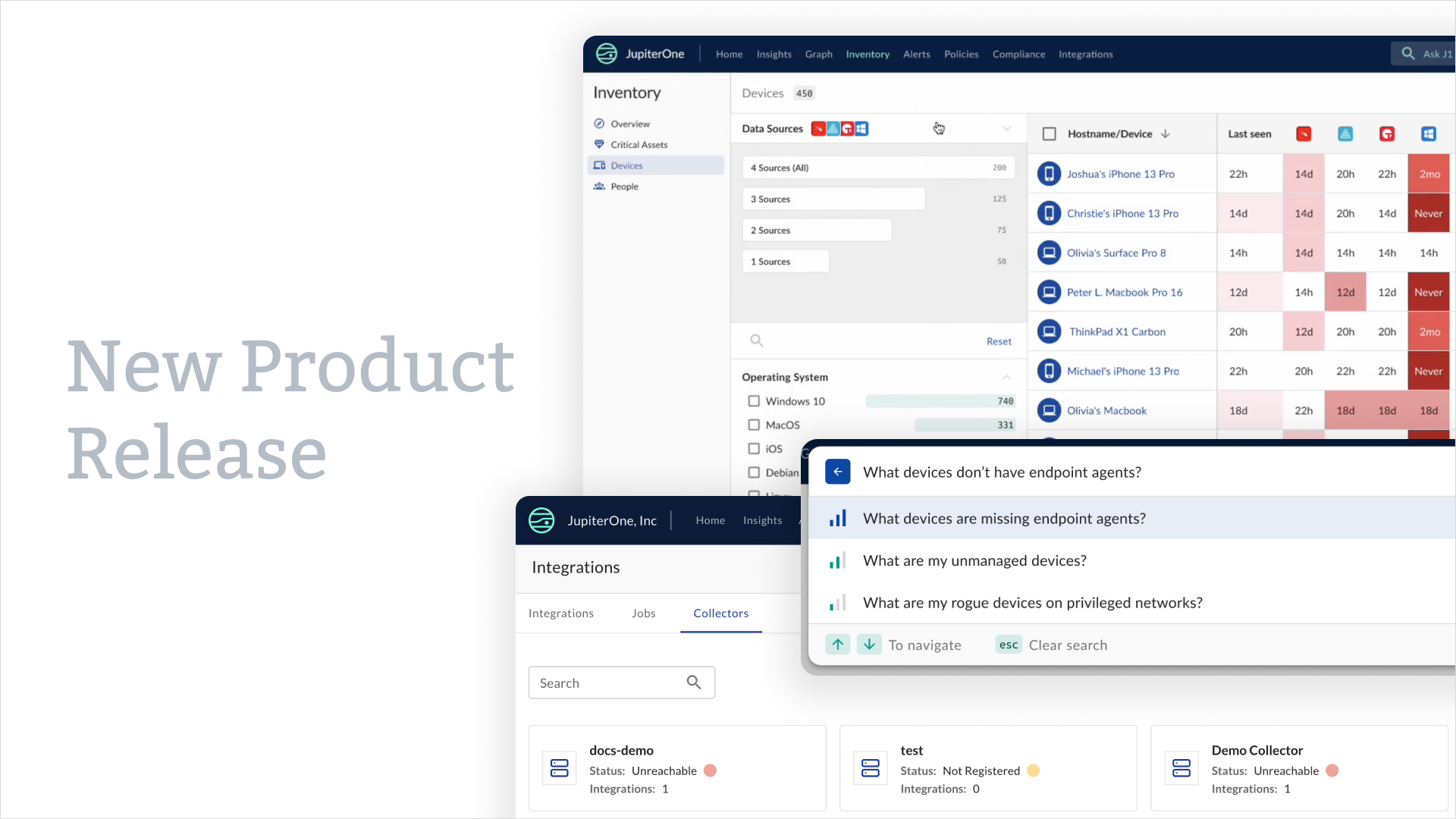
JupiterOne is releasing new functionality to better support customers' hybrid and on-premises devices and infrastructure along with new AI-powered search options.

Explore related assets, segment your data, and drill into your AWS environment with JupiterOne to get prescriptive with alerts and remediation.

Discover how the Jamf integration for JupiterOne enriches visibility with Mac device information and ownership.

Cyber asset management is vital to a secure and resilient digital infrastructure. Learn about its top challenges and how to overcome them.
- CAASM

Learn how these similar but different solutions can work together and create a more cyber-resilient environment.
- CAASM
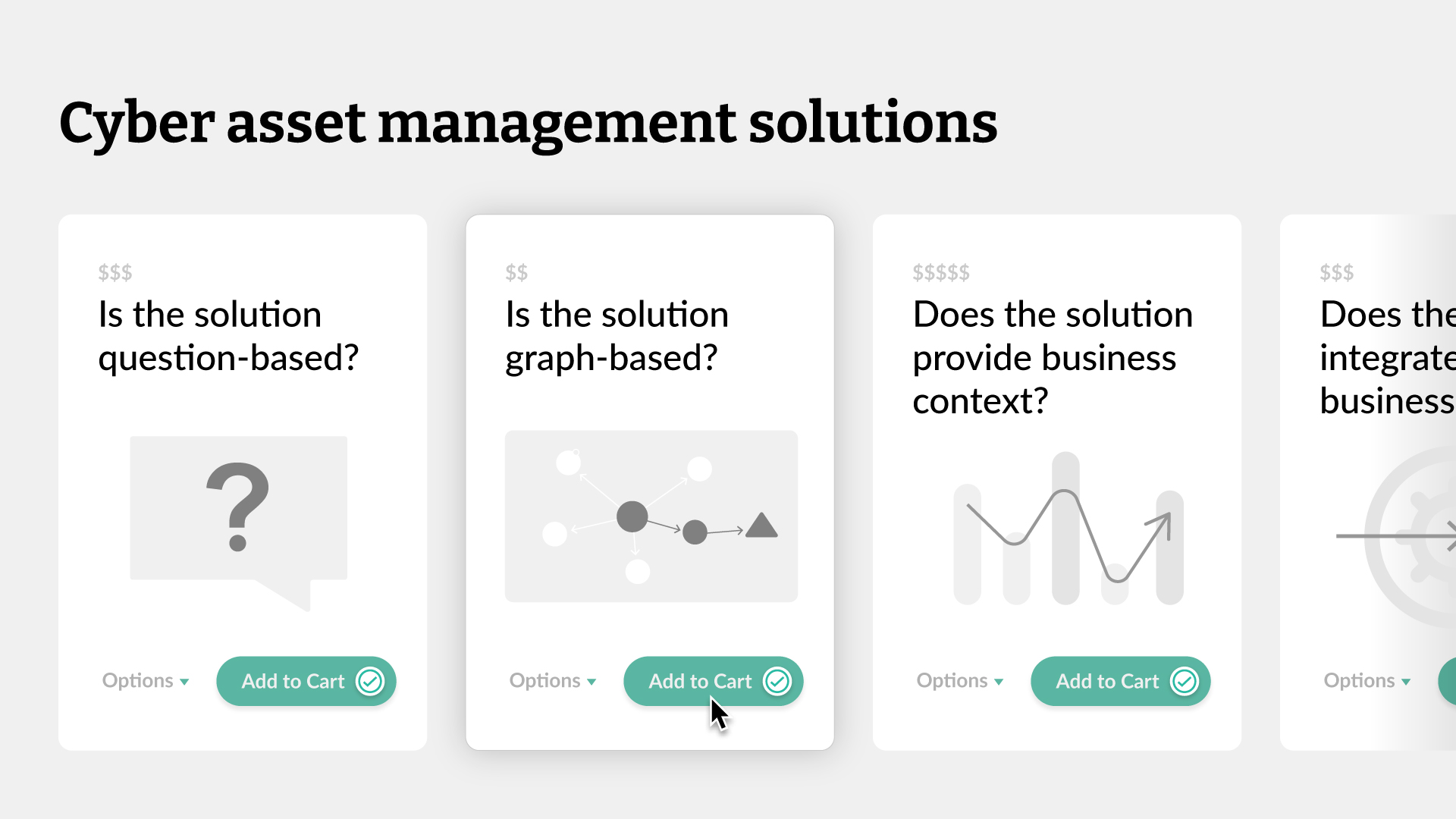
Finding the right cyber asset management solution takes work. Ask these five questions to find the solution that's fit for your business.
- CAASM

Attack surface management and vulnerability management often overlap but are both vital to an organization’s cybersecurity posture.
- CAASM
- Vuln Mgmt

JupiterOne VP of Marketing Rebecca Sanda shares her story behind becoming an LGBTQ Ally and the inclusive employee culture at JupiterOne.

When are Data Security Posture Management tools useful and how can JupiterOne be used for basic DSPM functions?

The 2023 SCAR report builds in some important contextual analysis of the findings, including company size breakdowns and CSP adoption details.

JupiterOne can assist many functions within your IT department, including one very visible and important team: Help Desk Support.

Cyber resilience starts with knowing which questions the organization should answer, across all levels, from the front lines to the Board of Directors.

Problem solving is at the core of what we do, from building a better product to helping our customers solve the most challenging cybersecurity and business problems.

RSA Conference 2023 has come and gone. There's quite a bit to come away with from the event - here are some of the things we learned here at JupiterOne.

Take a look at some of the key facts and considerations from the 2023 State of Cyber Assets Report.

The JupiterOne team spent some time checking out the most creative booths on the 2023 RSA Conference floor and came back with a top-5 list of their favorites.

The growing gap between team growth and attack surface, evident in the 2023 State of Cyber Assets Report (SCAR), drives teams to secure resources at scale.

JupiterOne AI is an artificial intelligence-powered, self-service experience harnessing the power and usability of AI/ML.

Secureworks' Alex Dyer demonstrates how his company uses JupiterOne to monitor and manage AWS Organizations across an enterprise environment.
- CAASM

JupiterOne can help organizations understand the impact of a recently discovered issue in Microsoft Azure that could lead to unauthorized access and possible attacks.
- Vuln Mgmt

The annual State of Cyber Assets Report (SCAR) analyzes data from organizations using JupiterOne to better understand today’s cybersecurity landscape.

Enterprises seeking to employ Cybersecurity Mesh Architecture can turn to JupiterOne as an invaluable CSMA accelerator and enabler.

Does cybersecurity awareness training work? Security leaders Sounil Yu and Juliet Okafor debate the question.

Adrian Sanabria, a practitioner with more than 20 years of experience, shared his use case for The Cyber Defense Matrix - visualizing breaches and incidents.
- IR

Continuing with lessons learned from Part 1 and the recent Automox deployment at JupiterOne, we look at how to use JupiterOne to simplify endpoint software deployment

Technology sales and customer success veteran Paul Forte joins JupiterOne as its new Chief Revenue Officer.

The Cyber Defense Matrix provides a framework to organize your security data and identify your cybersecurity gaps.

Streamline operations with the new Tines’ workflow automation integration in JupiterOne
.png)
With the rise of open source software comes the rise of vulnerabilities in code dependencies. To find and fix these issues, there are three key questions to answer.

We recently had a situation at JupiterOne which triggered curiosity in members of our security team. A Google Group, used as a distribution list, had a surprise membe

The new JupiterOne Query Builder streamlines your querying experience by eliminating errors, simplifying query builds, and reducing time to value.

We polled some of our engineering leaders to see what it takes to succeed. In part two, we see if their answers align with the CISOs we talked to.

As a preventative measure, Github will be deprecating the Mac and Windows signing certificates used to sign Desktop app versions 3.0.2-3.1.2 and Atom versions 1.63.0-

In part one of this two-part series, we polled some of our top security experts to see what it takes to succeed secure and manage resources effectively.

Take a look at the top 5 episodes from Season 1 of Cyber Therapy, a video podcast featuring the humans of cybersecurity!

Review of some of the notable new features and updates to JupiterOne from 2022.

Switching to a new technology solution can be a gamble. With the right information to make your decision, you can be guided to base your purchase on a validated econo

We’ve revamped the JupiterOne Homepage and Questions Library so you can spend less time asking questions and more time getting to the bottom of any issue.
.jpg)
Learn about the open source cybersecurity tools available to your organization, and why you should use them.
.png)
Traditional, relational databases are not equipped to meet the demands of a complex, cloud-native, hybrid, or multi-cloud environment. Luckily, graph databases can.

Kelly Shortridge, Fastly Senior Principal, Product Technology, offered her security predictions for 2023 as part of a CSA panel discussion webinar to close out 2022.

A lot of things go into creating an enterprise vulnerability management strategy. Learn how to build a strategy that will meet the unique needs of your organization.
- Vuln Mgmt

If you are a LastPass customer, the only thing standing between an attacker and your decrypted vault is a weak password. Find those easily with JupiterOne.

Incorporating a vulnerability management workflow will make your vulnerability management efforts and tools more effective and reliable.
- Vuln Mgmt

25 cybersecurity conferences we recommend (and will also attend!).

How long does it take you to find out you've become noncompliant? Continuous compliance solutions go beyond point-in-time checks to ensure compliance at all times.
- Compliance

We are releasing j1nuclei, an open-source tool to automate vulnerability scanning. The tool is available to anyone using the free version of JupiterOne.

Vulnerability management tools are an important part of enterprise cybersecurity. Choosing the right tool will make a huge difference in your cybersecurity program.
- Vuln Mgmt

Attack surface analysis is the process of identifying and mapping the areas in your attack surface that need to be reviewed for gaps and vulnerabilities by way of con

To help organizations of all sizes secure their cloud assets, JupiterOne announced a number of key initiatives with AWS this week at re:Invent.
- CSPM
- CAASM

The new Properties Panel and Managed Dashboards in the JupiterOne platform empower you to prioritize speed, efficiency, and organization!

In a recent debate on cybersecurity predictions for 2023, panelists disagreed on plenty. But they agreed: in 2023, security will give up on users as a line of defense

Lorem ipsum dolor sit amet, consectetur adipiscing elit. Suspendisse varius enim in eros elementum tristique. Duis cursus, mi quis viverra ornare, eros dolor interdum nulla, ut commodo diam libero vitae erat. Aenean faucibus nibh et justo cursus id rutrum lorem imperdiet. Nunc ut sem vitae risus tristique posuere.
- This is some text inside of a div block.
- This is some text inside of a div block.
- This is some text inside of a div block.
- This is some text inside of a div block.
- This is some text inside of a div block.